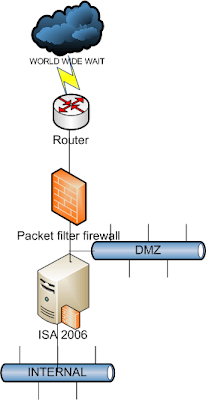
Let me explain a little of this diagram above
- My first firewall is my traditional firewall. This box should filter all those incoming traffic not explicitly allowed by your organization. Outgoing packets can go freely without restrictions. Later, i will share why you can confidently do this and therefore reduce complexity in your network.
- The DMZ is placed in between the ISA and my 1st FW. Please note, this server is now “published” by the 1st FW and not ISA. In here, you should only keep boxes that will not contain data for a long time (a temp repository) like a web server, smtp server etc..
- Finally, the ISA comes in. ISA’s default GW is the 1st FW.
Lets talk about NAT.
1stFW (liveIP) –NAT/Route –> ISA –NAT/Route > Internal Networks
So, the DMZ IP network will act as ISA’s external network but you can still use private IP addresses. Some of these IPs will be the publishing IP for your internal networks, just imagine them as public IPs.Another huge benefit of having ISA there is to do Proxy-ing. Now that i’ve mentioned to allow all traffic outbound on the 1stFW, ISA takes the responsibility to ensure certain ports and protocols are allowed. Doing this, having one place for internal to external traffic control simplifies management of security in your network. Users can be authenticated and authorized to sites or services that are allowed by your organization policies.Even VPN should work fine in this design where ISA can terminate the VPN connection after a NAT done by the 1st FW.

Sanjay,
Cool article. This will kill most of the consultant out there. Thanks for the detail explanation.
Haha, bro, don’t intend to “kill” anyone, just wanna’ help… Thanks for reading tho :), oh and by the way, i love your blog’s unique posts.