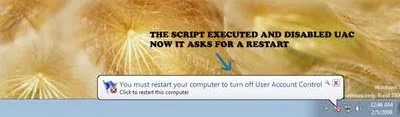
I read a recent online article that UAC can be switched off without user intervention in W7. I was curious to test it out. So i powered up my good ol’ VM running W7 and tested the script. Firstly i logged on as a “normal” user, the script “died” goes about all its steps, but at the point of changing the UAC, it fails, simply because you need to be admin to do that. So, lets try with admin..
True enough, the script kinda worked. And UAC was disabled after the restart. Ok, you may be thinking this is crazy and there goes Windows 7 security! Hang on, its not so much the case. Why?
- You must be logged on as an Administrator group member to make this work
- Windows tells you that UAC has been turned off (if you know you didn’t do this, you can easily go turn it back on)
- The script must be executed by someone or something, meaning, a intervention is required, not automation.
- You can turn on UAC to notify you of changes, therefore, apps like this won’t run.
- So the conclusion is, its not much of a threat. It’s like asking a user to run formatmypcvirus.exe and the user runs it, of course la..they will be compromised.
Perhaps Microsoft could make it a little more difficult to change UAC by enabling UAC before UAC can be modified. According to Microsoft, this is not a bug and the case is closed..hmm..
Microsoft’s predicament:
The change we made in Windows 7 default UAC settings is that any operation that is necessary to manage windows will not require an elevation – which in technical terms translates into a white list of trusted action / binaries which the user can make perform without UAC prompting from an elevation. This list does include windows file operations
Source script: Rafael Rivera http://www.withinwindows.com/